Virtual Firewall - Introduction to the FireRack
[Index]
[Next Chapter: Overview of the Virtual Firewall Control Panel]
Chapter 1: Introduction to the FireRack
The Netservers FireRack firewall is an Internet security appliance designed to provide highly compartmentalised security with devolved management. It is hence ideally suited for environments such as co-location hosting or college networks where badly maintained or untrustworthy computers on the same network as yours could otherwise pose it a threat.
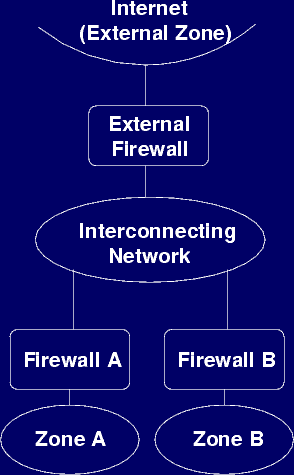
The FireRack architecture is based around the concept of 'security zones'. A security zone is either a single computer or a group of computers that are only able to talk directly to each other. All communication between a computer within a security zone and any other computer outside of that zone must be allowed by the firewall rules for that zone. For two computers in two different zones on the same FireRack firewall to inter-communicate, the firewall rules for both security zones must allow this. This compartmentalisation prevents the security of one zone from being compromised by changes to the configuration of another zone. Administration of each security zone can hence be delegated to different persons in a safe manner.
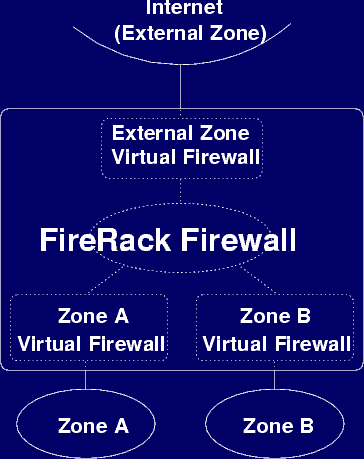
It is this combination of compartmentalisation and delegation of a zone that constitutes a FireRack Virtual Firewall. Each virtual firewall effectively acts on network traffic as if it were a separate physical firewall connected between the zone and a central interconnecting network, as illustrated below, and can be managed independently just as each real firewall could.
|
A Compartmentalised Network
|
A Compartmentalised Network
|
Often, a security zone will correspond to a separate physical network or to an IEEE 802.1q tagged VLAN, since this can provide full segregation between zones and prevent hostile computers bypassing the firewall. A FireRack can support over 4000 VLANs on each physical interface. Our recommended configuration for Internet Service Providers is to use VLAN-capable network switches for connecting all customer servers they host, and allocate a separate VLAN to each customer. (The FireRack also has other methods for segregating zones where it is not feasible to use separate LANs or VLANs: you will need to consult with your service provider if you wish to know the specifics of how your zone is implemented.)
Each virtual firewall has the following features:
- Dual-management capability (by customer and service provider)
- Stateful packet inspection filtering
- Destination and/or Source Network Address Translation (redirection and masquerading)
- PPTP server accounts for secure remote access
- User-friendly web based control panel
- Logging and graphing of traffic bandwidth usage
FireRack firewalls are configured using a FireRack Management Server. Each management server can manage many FireRack firewalls and virtual firewalls, potentially providing each administrator with a single point of management for managing all their firewalls.
[Index] [Next Chapter: Overview of the Virtual Firewall Control Panel]